COMPUTER REPAIR SHOP – USED COMPUTERS FOR SALE
We fix all computer problems you may be experiencing We remove all type computer viruses. Laptop Repairs performed in your home or business, Cant get into Windows, black screen, blue screen of death, rootkit, spyware, malware, email problems and more.

Online Computer Support Services
Providing Fast and affordable onsite local service for the following zip codes in South Florida. We buy and recycle broken computers.
ONSITE REPAIR IN BROWARD ZIPCODES: 33066 33073 33330 33065 33067
33071 33076 33004 33314 33325 33328 33441 33442 33301 33304 33306 33308 33309 33311 33312 33315 33316 33394 33009 33019 33020 33021 33023 33313 33319 33063 33025 33027 33068 33334 33024 33026 33028 33029 33317 33322 33324 33388 33060 33061 33062 33064 33069 33332 33323 33351 33321 33326 33327 33331 33305 33238 33242 33243 33245 33247 33255 33256 33257 33261 33265 33266 33269 33280 33283 33296
We Optimize and Clean your pc at very reasonable rates, fast computer virus removal, Call us for a complete tune-up and feel the difference in speed and performance for both PC and Apple iMac and Macbook Pro online computer repair and damage or broken laptop screen repair replacement. Sales, service Installation of LED Screens / LCD Screen Panel cover protector.
IT Technical Assistance
We carry and sale full stock of pc and apple parts for both desktop and laptops. Local Computer Repair Fort Lauderdale – South Florida
MIAMI DADE: 33101 33102 33107 33110 33111 33114 33116 33121 33122 33124 33125 33126 33127 33128 33129 33130 33131 33132 33133 33134 33135 33136 33137 33138 33142 33143 33144 33145 33146 33147 33148 33150 33151 33152 33153 33154 33155 33156 33157 33158 33159 33161 33162 33163 33164 33165 33166 33167 33168 33169 33170 33172 33173 33174 33175 33176 33177 33178 33179 33180 33181 33182 33183 33184 33185 33186 33187 33188 33195 33196 33197 33199 33231 33233 33234
Emergency computer virus removal in Miami, same day computer repair in Miami, Sunrise same day computer repair near Boca Raton, fast computer repair, Margate emergency computer repair, Pompano Beach computer repair, Davie same day virus removal, Margate same day virus removal, same day laptop screen replacement installation, Laptop Motherboard repair miami.
Local Computer Help, Virus Removal, Repairs Specialist for all laptop manufacturer
Acer Laptop Repair – TravelMate, Extensa, Ferrari, Aspire One
Apple Computer Laptop – MacBook, MacBook Air, MacBook Pro, Imac G4 G5 Ibook
Dell Computer Repair – Inspiron, Latitude, Precision, Studio, Vostro, XPS, Studio XPS, Alienware
Asus Laptop Repair – Asus Eee, Lamborghini Fujitsu – LifeBook, Stylistic
Lenovo Laptop Repair – ThinkPad, IdeaPad, 3000, IBM Sony Laptop Repair – VAIO Series
Compaq Computer Repair – Armada, Concerto, Contura, Presario, ProSignia, LTE, Mini, SLT
HP Laptop Repair – Hewlett-Packard, HP Pavilion, HP Omnibook Envy EliteBook ProBook
Gateway Computer – Solo & Pro Series Samsung Computer Repair – Sens, eMachines, Pro
Toshiba Laptop Repair – Dynabook, Portege, Tecra, Satellite, Qosmio, Libretto
Do you have a Broken Computer? Not starting up? Making noise? Black screen, Blue screen? We fix it in 20 minutes.
Computer Repair near me, Local Service and Repair in your home or business at no extra charge! Super Fast Repair Services for all brands
CALL 754-234-5598
We are rated 5 star and listed on the top 10 most valuable and fastest computer repair in the south florida area. Please check our customer reviews and ratings on Google Places,Yelp, Bing, Yahoo and google maps. Satisfaction guaranteed.
Located in Fort Lauderdale, and Locally Serving all South Florida, Broward, Dade and Palm Beach county, from Miami to Boca Raton, Boynton beach and South Palm Beach and online nationwide services.
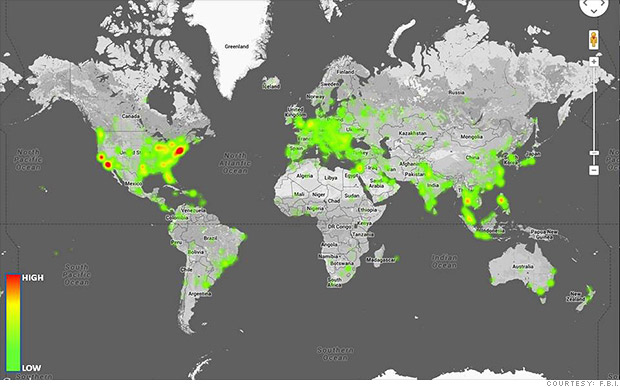 Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.
Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.

