The waves of celebrities nude photos have not yet stopped completely, and a new privacy threat has emerged exposing tens of thousands of private photographs and videos of innocent users are circulating over the Internet.
The personal image that are believed to be sent through Snapchat — the ephemeral messaging service that allows users to send pictures that should disappear after a few seconds — has been floating on the image based 4chan’s notorious /b/ board since last night. The incident was result of a security breach in an unofficial third-party app for Snapchat.
Earlier this week, an anonymous 4chan user claimed to have obtained images on Snapchat and then the user warned of releasing thousands of nude videos and images sent using Snapchat soon in an event dubbed ‘The Snappening’.
Previously, It was believed that the official SnapChat mobile app or its servers had been hacked by the hackers, and the third-party Snapchat client app has been collecting every photo and video file sent through the messaging service for years, giving hackers access to a 13GB private Snapchat files.
But Snapchat has denied that its service was ever compromised. Earlier today, Snapchat issued a statement about the “Snappening” and blamed its consumers for using unofficial and unauthorized third-party apps.
“We can confirm that Snapchat’s servers were never breached and were not the source of these leaks,’ a Snapchat representative said in a statement. “Snapchatters were victimised by their use of third-party apps to send and receive Snaps, a practice that we expressly prohibit in our Terms of Use precisely because they compromise our users’ security. We vigilantly monitor the App Store and Google Play for illegal third-party apps and have succeeded in getting many of these removed.“
The most worrying part for the users is that Snapchat was right. The personal data is supposed to be obtained from a website called SnapSaved.com — an external app used by a number of Snapchatters in order to save Snapchat photos without the sender knowing — which has been inactive for the past few months and is apparently independent of the official Snapchat service.
However, Business Insider has pointed to SnapSaved.com, a site which is no longer functional, and the SnapSave app as potential sources of the leak. Meanwhile, an assortment of photos has been traced back to SnapchatLeaked.com — site also posted personal and nude photos of Snapchat users, indicating that the photos could have been circulating for months.
“The Snappening” is named in reference to the recent celebrity nude photos leak that was called “The Fappening.” The incident comes just weeks after thousands of celebrity nude images were leaked online through 4chan website, following a hack of Apple’s iCloud.
Snapchat was first hacked in December 2013 when 4.6 million Snapchat users were exposed in a database breach. Later, the denial-of-service attack and CAPTCHA Security bypass The most worrying part for the users is that Snapchat was right. The personal data is supposed to be obtained from a website called SnapSaved.com — an external app used by a number of Snapchatters in order to save Snapchat photos without the sender knowing — which has been inactive for the past few months and is apparently independent of the official Snapchat service.
However, Business Insider has pointed to SnapSaved.com, a site which is no longer functional, and the SnapSave app as potential sources of the leak. Meanwhile, an assortment of photos has been traced back to SnapchatLeaked.com — site also posted personal and nude photos of Snapchat users, indicating that the photos could have been circulating for months.
“The Snappening” is named in reference to the recent celebrity nude photos leak that was called “The Fappening.” The incident comes just weeks after thousands of celebrity nude images were leaked online through 4chan website, following a hack of Apple’s iCloud.
Snapchat was first hacked in December 2013 when 4.6 million Snapchat users were exposed in a database breach. Later, the denial-of-service attack and CAPTCHA Security bypass vulnerabilities were discovered by the researchers at the beginning of this year.
Please Visit our Computer News Website and Blog
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere
Fort Lauderdale, Miami, Boca Raton, Boynton Beach and all South Florida
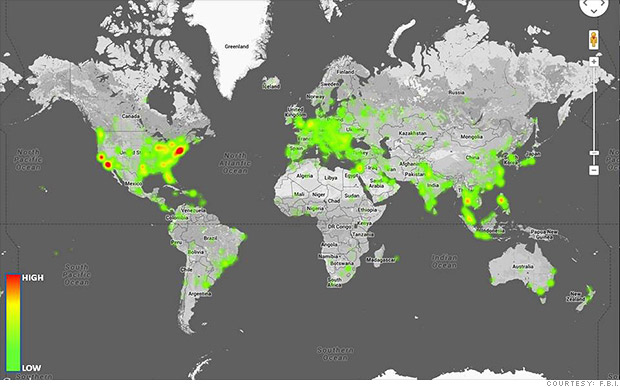 Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.
Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.