Computer hacker forums lit up last week as Federal Bureau of Investigation agents and police in 17 countries began knocking on doors, seizing computers and making arrests.
On the popular websites where cyber criminals buy and sell software kits and help each other solve problems, hackers issued warnings about police visits to their homes.
The hackers quickly guessed that a major crackdown was underway on users of the malicious software known as Blackshades.
The FBI and prosecutors in the Manhattan U.S. attorney’s office announced the results of that probe on Monday: More than 90 arrests worldwide.
The malware sells for as little as $40. It can be used to hijack computers remotely and turn on computer webcams, access hard drives and capture keystrokes to steal passwords — without victims ever knowing it.
Related: Beware, your computer may be watching you
Criminals have used Blackshades to commit everything from extortion to bank fraud, the FBI said.
Last week, watching it all play out were about two dozen FBI cybercrime investigators holed up in the New York FBI’s special operations center, high above lower Manhattan.
Rows of computer screens flickered with updates from police in Germany, Denmark, Canada, the Netherlands and elsewhere. Investigators followed along in real time as hundreds of search warrants were executed and suspects were interviewed.
The sweep, capping a two-year operation, is one of the largest global cybercrime crackdowns ever. It was coordinated so suspects didn’t have time to destroy evidence. Among those arrested, in Moldova, was a Swedish hacker who was a co-creator of Blackshades.
“The charges unsealed today should put cyber criminals around the world on notice,” said Leo Taddeo, chief of the FBI’s cybercrime investigations in New York. “If you think you can hide behind your computer screen — think again. ”
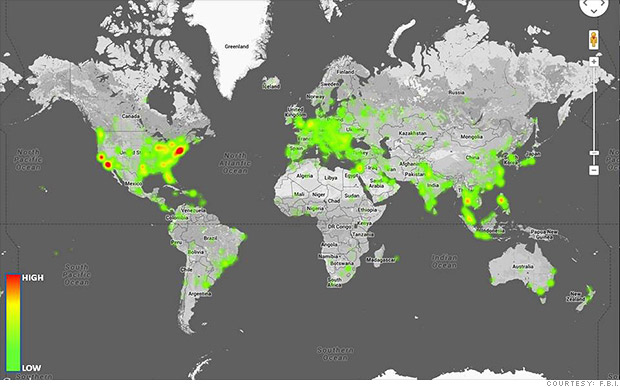 Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.
Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.
700,000 victims around the world: Inside the FBI special operations center, six large computer monitors displayed key parts of the probe. Agents kept an eye on one screen showing a popular website where Blackshades was sold. The site was taken down by the FBI.
Another monitor showed a heatmap of the world displaying the locations of the 700,000 estimated victims, whose computers have been hijacked by criminals using the Blackshades software. Splotches of green on the map indicated concentrations of infected computers in highly populated parts of the U.S., Europe, Asia and Australia.
The FBI said that in just a few years Blackshades has become one of the world’s most popular remote-administration tools, or RATs, used for cybercrime.
Taddeo said the unprecedented coordination with so many police agencies came about because of concern about the fast growth of cybercrime businesses.
“These cyber criminals have paid employees, they have feedback from customers — other cyber criminals — to continually update and improve their product,” Taddeo said recently. While he spoke, agents took calls from counterparts working the case in more than 40 U.S. cities.
Blackshades had grown rapidly because it was marketed as off-the-shelf, easy to use software, much like legitimate consumer tax-preparation software.
“It’s very sophisticated software in that it is not very easy to detect,” Taddeo said. “It can be installed by somebody with very little skills.”
Please Visit our Computer News Website and Blog
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere