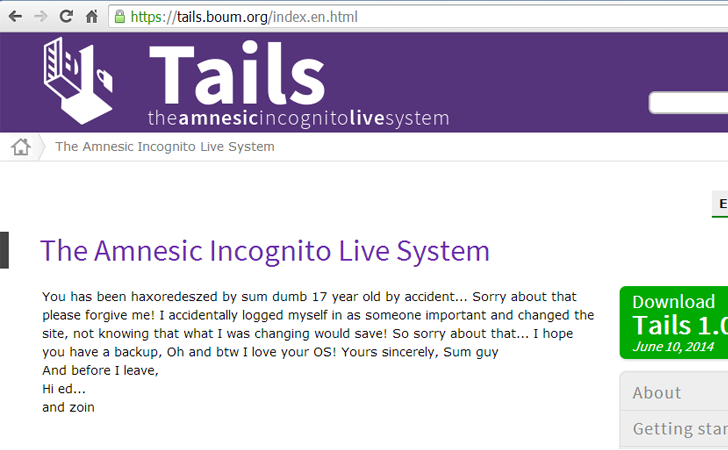
Just a few hours ago, the Official website of the Tails Operating System has been hacked and it appears that a self-proclaimed 17-year old hacker breached and defaced it.
Tails is a Linux-based highly secure Operating System, specially designed and optimized to preserve users’ anonymity and privacy. Hacker, who named himself “Sum guy”, managed to access the website as administrator and edited the homepage content with the following message:
You has been haxoredeszed by sum dumb 17 year old by accident… Sorry about that please forgive me! I accidentally logged myself in as someone important and changed the site, not knowing that what I was changing would save! So sorry about that… I hope you have a backup, Oh and btw I love your OS! Yours sincerely, Sum guy
And before I leave,
Hi ed…
and zoin
Defaced Link: https://tails.boum.org/index.en.html. However, all other pages on the Tails website are working just fine, but at this moment it is not clear whether the hacker has also modified the OS Image or not. So readers are advised to do not download the Tails OS from the website, at least for a few days.
Tails, also known as ‘Amnesiac Incognito Live System‘, is free software based on Debian GNU/Linux and you install it on a DVD or USB drive, boot up the computer from the drive. This allows you to work on a sensitive file on any computer and prevent the data being recovered after the computer is turned off.
Tails was reportedly used by the NSA Whistle-blower Edward Snowden in discussions with journalists because it includes a range of tools for protecting your data by means of strong encryption.
Please Visit our Computer News Website and Blog
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere
Fort Lauderdale, Miami, Boca Raton, Boynton Beach and all South Florida




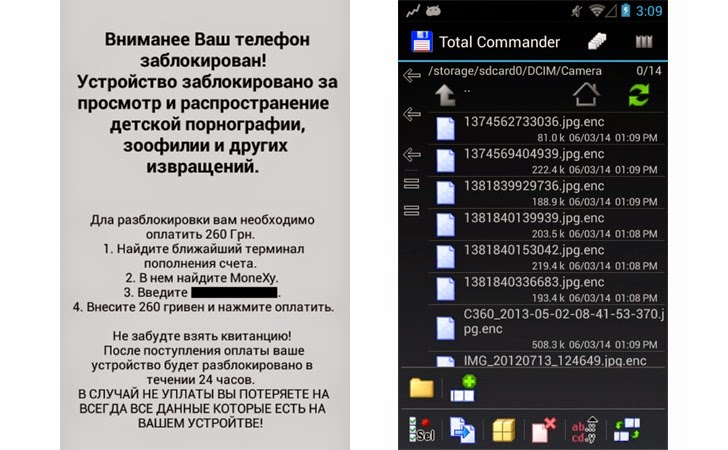
![[IMG]](https://www.neowin.net/images/uploaded/shutterstock-businessman-looking-phone_story.jpg)

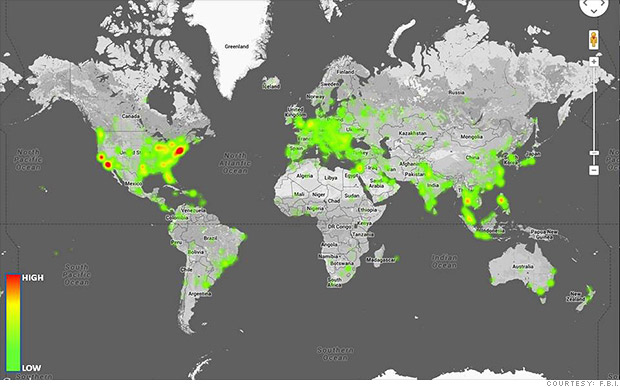 Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.
Officials say Blackshades was used to illegally access the computers of 700,000 victims around the world, as shown in this FBI heatmap.