Researchers have warned users of Android devices to avoid app downloads from particularly unauthorized sources, since a new and sophisticated piece of malware is targeting Android users through phishing emails.
The malware, dubbed SandroRAT, is currently being used by cybercriminals to target Android users in Poland via a widely spread email spam campaign that delivers a new variant of an Android remote access tool (RAT).
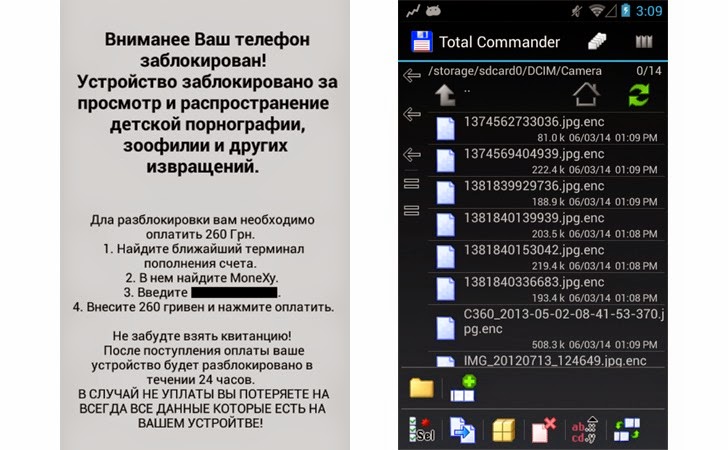
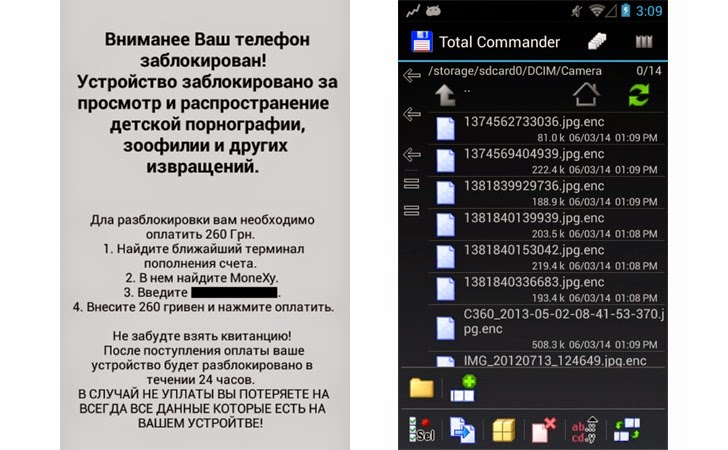
The emails masquerade itself as a bank alert that warns users of the malware infection in their mobile device and offers a fake mobile security solution in order to get rid of the malware infection.
The mobile security solution poses as a Kaspersky Mobile Security, but in real, it is a version of SandroRAT, a remote access tool devised for Android devices, whose source code has been put on sale on underground Hack Forums since December last year.
A mobile malware researcher at McAfee, Carlos Castillo, detailed the new variant of Android remote access trojan over the weekend. According to the researcher, the package spread via phishing campaign is capable of executing several malicious commands on the infected devices.
SandroRAT gives the attacker an unrestricted access to sensitive details such as SMS messages, contact lists, call logs, browser history (including banking credentials), and GPS location data stored in Android devices and store all the data in an “adaptive multi-rate file on the SD card” to later upload them to a remote command and control (C&C) server.
“Spam campaigns (via SMS or email) are becoming a very popular way to distribute Android malware, which can steal personal information or even obtain complete control of a device with a tools like SandroRat,” wrote Carlos Castillo. “This attack gains credence with the appearance of a bank offering security solutions against banking malware, a typical behavior of legitimate banks.”
This new version of SandroRAT also has a self-update feature in it and it can install additional malware through user prompts for such actions. The malware gives the attacker full control over the messages, who can intercept, block and steal incoming messages, as well as insert and delete them.
It also appears that the attacker can send multimedia messages with specific parameters sent by the C&C server and can also record nearby sounds using the device’s mic.
Castillo also notes that the SandroRAT variant of malware had decryption capabilities for older releases of Whatsapp messaging app. But, the users running the latest version of Whatsapp in their Android devices are not vulnerable because the developers adopted a stronger encryption scheme.
“This decryption routine will not work with WhatsApp chats encrypted by the latest version of the application because the encryption scheme (crypt7) has been updated to make it stronger (using a unique server salt),” Castillo explained. “WhatsApp users should update the app to the latest version,” he advised.
Users are advised to avoid application downloads from unauthorized sources, particularly when the app download link is send through an email. Good practice is to always prefer downloading apps from the Google Play Store or other trusted sources.
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere
Fort Lauderdale, Miami, Boca Raton, Boynton Beach and all South Florida