A new zero-day vulnerability that resides in all versions of Internet Explorer has been spotted in the wild, Microsoft confirmed late Saturday.
The vulnerability, which could allow remote code execution, is being used in “limited, targeted attacks,” according to an advisory issued by Microsoft. While all versions of the web browser, IE 6 through 11, are affected by the vulnerability, attacks are currently targeting IE versions 9, 10 and 11, according to security firm FireEye, which first reported the flaw Friday.
The attack leverages a previously unknown “use after free” vulnerability — data corruption that occurs after memory has been released — and bypasses both Windows DEP (data execution prevention) and ASLR (address space layout randomization) protections, according to FireEye.
The vulnerability is currently being exploited by a group of hackers targeting financial and defense organization in the US, FireEye told CNET.
“The APT [advanced persistent threat] group responsible for this exploit has been the first group to have access to a select number of browser-based 0-day exploits (e.g. IE, Firefox, and Flash) in the past,” FireEye said. “They are extremely proficient at lateral movement and are difficult to track, as they typically do not reuse command and control infrastructure.”
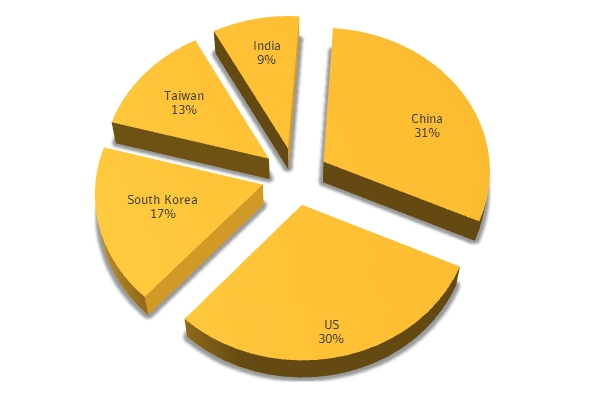
FireEye said the flaw was significant because it affects more than a quarter of the total browser market.
“Collectively, in 2013, the vulnerable versions of IE accounted for 26.25% of the browser market,” FireEye said in its advisory.
An attack could be triggered by luring visitors to a specially crafted web page, Microsoft explained.
“The vulnerability exists in the way that Internet Explorer accesses an object in memory that has been deleted or has not been properly allocated,” Microsoft said. “The vulnerability may corrupt memory in a way that could allow an attacker to execute arbitrary code in the context of the current user within Internet Explorer.”
Microsoft said it is investigating the vulnerability and may issue an out-of-cycle security update to address the issue.
Please visit ccrepairservices.com
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere