A new file-encrypting ransomware was discovered today by BartBlaze called CryptoGraphic Locker. Just like other encrypting ransomware, this infection will scan your your data files and encrypt them so that they are unusable. The infection will then display a ransom note that requires you to purchase the decryption key in order to decrypt your files. The initial cost to purchase the key is .2 BTC, or approximately $100 USD, which makes this one of the cheaper ransoms that we have seen in a long time. Though the ransom starts out small, there is a 24 hour timer built into the application that will increase the ransom amount each time it hits 0.
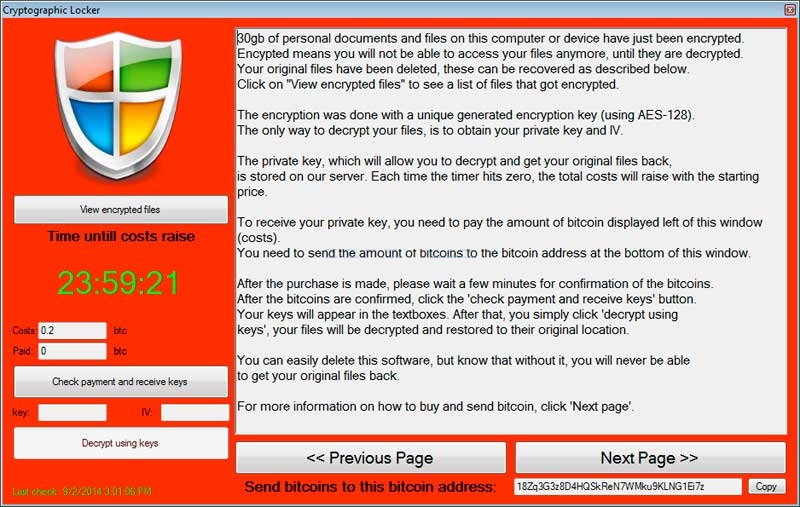
When you are infected with CryptoGraphic Locker, the application will configure itself to start when you login to Windows. It will then scan your drives for data files and create new encrypted copies using AES encryption and then delete the old ones. These new files will be renamed to have the extension .clf. A list of all encrypted files will be stored in the %Temp%\CryptoLockerFileList.txt file. The data files that CryptoGraphic Locker targets are:
.odt,.ods,.odp,.odm,.odc,.odb,.doc,.docx,.docm,.wps,.xls,.xlsx,.xlsm,.xlsb,.xlk,.ppt,.pptx,.pptm,.mdb,.accdb,.pst,.dwg,.dxf,.dxg,.wpd,.rtf,.wb2,.mdf,.dbf,.psd,.pdd,.pdf,.eps,.ai,.indd,.cdr,.dng,.3fr,.arw,.srf,.sr2,.mp3,.bay,.crw,.cr2,.dcr,.kdc,.erf,.mef,.mrw,.nef,.nrw,.orf,.raf,.raw,.rwl,.rw2,.r3d,.ptx,.pef,.srw,.x3f,.lnk,.der,.cer,.crt,.pem,.pfx,.p12,.p7b,.p7c,.jpg,.png,.jfif,.jpeg,.gif,.bmp,.exif,.txt
When the infection has finished encrypting your data it will display a ransom screen that explains how you can pay the ransom and decrypt your files. Unlike other file-encrypting ransomware that have been released lately, instead of using a decryption site, the malware application itself allows you to make payments, receive your decryption keys, enter your key to decrypt files, etc. While the infection is running it will also terminate the following applications if they are started or are running: Process Hacker, MalwareBytes, Spyhunter, Msconfig, Task Manager, Registry Editor, System Restore, or Process Explorer.
Last, but not least, the infection will also change your Windows desktop background to the background below. Suprisingly, it uses the CryptoLocker name in the wallpaper instead of the CryptoGraphic Locker name that it uses in the application window.

At this time the Command & Control servers are down, so there is no way to pay the ransom. There is, though, some good news for those who are infected. This ransomware does not delete files using a secure deletion method and does not wipe your system restore points. Therefore you can use a file recovery tool to undelete your files or a program like Shadow Explorer to restore your files from Shadow Volume Copies. Information on how to restore your files from Shadow Volume Copies can be found in the CryptoLocker guide.
Thanks to BartBlaze, Decrypterfixer, and Cody Johnston for providing info on this malware.
File additions and registry changes are:
%Temp%\CryptoLockerFileList.txt %Temp%\wallpaper.jpg <Path to Dropper>\<random.exe HKCU\Control Panel\Desktop\Wallpaper "C:\Users\User\AppData\Local\Temp\wallpaper.jpg"(old value="") HKCU\Control Panel\Desktop\WallpaperStyle "1"(old value="10") HKCU\Software\Microsoft\Windows\CurrentVersion\Run\CLock
Please Visit our Computer News Website and Blog
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere
Fort Lauderdale, Miami, Boca Raton, Boynton Beach and all South Florida
Loading image
Click anywhere to cancel
Image unavailable

Loading image
Click anywhere to cancel
Image unavailable
