Attackers have been leveraging the FlashPack Exploit Kit to peddle the CryptoWall 2.0 ransomware on unsuspecting visitors to sites such as Yahoo, The Atlantic and AOL. Researchers believe that for about a month the malvertising campaign hit up to 3 million visitors and netted the attackers $25,000 daily.
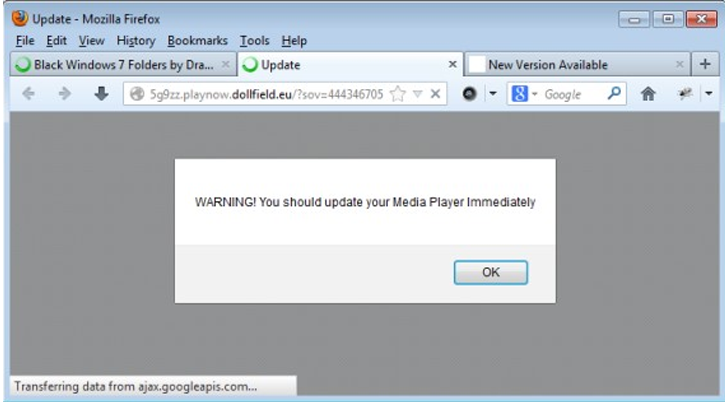
According to experts at Proofpoint, a firm that primarily specializes in email security, the exploit kit targeted a vulnerability in Adobe Flash via users’ browsers to install the ransomware on users’ machines.
Malvertising is an attack that happens when attackers embed malicious code – in this case code that led to the latest iteration of CryptoWall – into otherwise legitimate ads to spread malware via drive-by downloads. Users can often be infected without even clicking on anything.
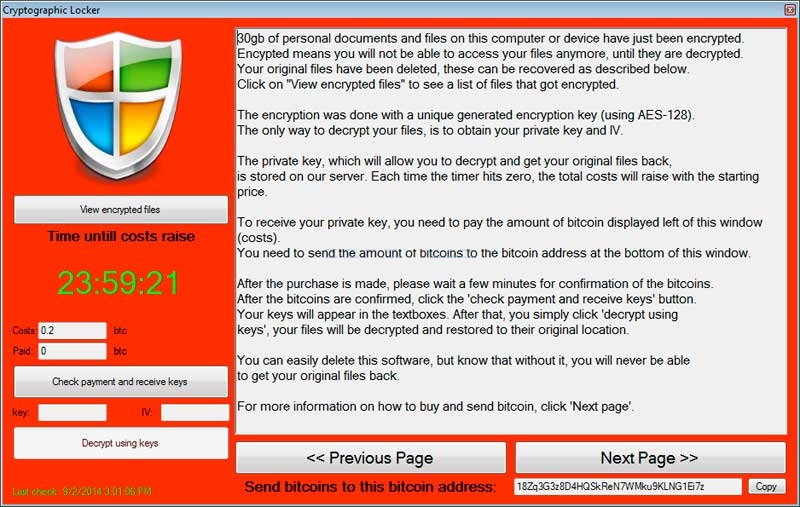
CryptoWall, which takes users’ files, encrypts them with rigid RSA-2048 encryption, then asks for a fee to decrypt them, made a killing earlier this summer. In August it was reported that the ransomware made more than $1.1 million for its creators in just six months.
Similar to Critoni/Onion, a ransomware dug up in July, CryptoWall 2.0 downloads a TOR client on the victim’s machine, connects to a command and control server and demands users send Bitcoin – $500 worth – to decrypt their files. Since the campaign lasted about a month, from Sept. 18 to this past Saturday, researchers are estimating that 40 of the campaign’s Bitcoin addresses collected at least 65 BTC each, a number that roughly translates to $25,000 a day.

Proofpoint claims that high ranking sites such as AOL, The Atlantic, Match.com and several Yahoo subdomains such as their Sports, Fantasy Sports and Finance sites, were spotted serving up the tainted ads. Other sites lesser known in the U.S. such as Australia’s Sydney Morning Herald, The Age, and the Brisbane Times, were reportedly also doling out the ads.
While the campaign started a month ago the firm claims things didn’t start to ramp up until recently.
“After crossing a threshold level, it became possible to associate the disparate instances with a single campaign impacting numerous, high-traffic sites,” Wayne Huang, the company’s VP of Engineering, said of the campaign.
The firm claims it worked quickly to notify those involved in the campaign, including the ad providers, and as of this week, believes the situation has been nullified.
Last month researchers with Barracuda Labs found a CryptoWall variant with certificate signed by Comodo being distributed through ads on a handful of different websites. None of those sites were nearly as trafficked as those spotted by this most recent campaign however. The Alexa rankings for Yahoo (4), AOL (37), Match (203), and The Atlantic (386) place them within the top 500 of the internet’s most popular sites, something that likely upped the campaign’s exposure level.
Please Visit our Computer News Website and Blog
for latest computer repair and online news.
Local and Online Virus removal and computer repairs anytime, anywhere
Fort Lauderdale, Miami, Boca Raton, Boynton Beach and all South Florida