
I think you haven’t forgotten the massive data breach occurred at TARGET, the third-largest U.S. Retailer during last Christmas Holidays. People shop during Black Friday sales in which over 40 million Credit & Debit cards were stolen, used to pay for purchases at its 1500 stores nationwide in the U.S.
TARGET officially confirmed that the encrypted PINs (personal identification numbers) of payment cards were stolen in the breach, since the stolen pin data were in encrypted form so they were confident that the information was “Safe and Secure”, because PIN cannot be decrypted without the right key.
The Breach was caused by a malware attack, that allowed the criminals to manipulate Point of Sale (PoS) systems without raising red flags and the card numbers compromised in the breach are now flooding underground forums for sale.
Possibly a group of Eastern European cyber criminals who specializes in attacks on merchants and Point-of-Sale terminals either attached a physical device to the PoS system to collect card data or they infected the PoS system with malware which sniffed the card data as it passes through a PoS system.
However, the hackers have all 40 Million payment card details, but the PINs are encrypted with Triple-DES (Data Encryption Standard), which is a highly secure encryption standard used broadly throughout the U.S.
Recently, The Cyber Intelligence firm IntelCrawler noticed that a group of individuals are discussing in underground hacking forums, attempting to decrypt a 50GB dump of Triple DES (3DES) encrypted PIN numbers believed that it belongs to TARGET breach. They asked for a ‘pro hacker’ to decrypt the information at a fee of $10 per line.
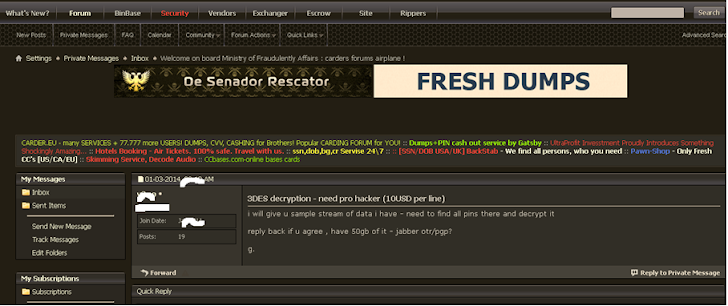
IntelCrawler also claims that cracking the Triple-DES may be a slow process, but not impossible and vulnerable to brute-force attack using cracking tools i.e. John the Ripper.
Security researcher, Robert Graham writes a blog post, suggested that hackers can get PINs without decrypting them, because two identical PINs decrypt to the same value.
For example, let’s say that the hacker shopped at Target before stealing the database. The hacker’s own debit card information will be in the system. Let’s say the hacker’s PIN was 8473. Let’s say that these encrypts to 98hasdHOUa. The hacker now knows that everyone with the encrypted PIN of “98hasdHOUa” has the same pin number as him/her, or “8473”. Since there is only 10,000 combination of PIN numbers, the hacker has now cracked 1000 PIN numbers out of 10 million debit cards stolen. He recommended that TARGET should at least salt the encryption, to make it more difficult for crackers.
ONLINE COMPUTER REPAIR SERVICES AND NEWS AT
www.ccrepairservices.com